BTech Cyber Security deals with the study of Information Security and Network Security.
Computer networks have been widely adopted by businesses of all sizes for their daily operations, as they are cost-effective and time-efficient.
Business organizations store data on computers and servers and transmit most of their information through email and websites using the internet over wireless and wired networks.
They are prone to cyberattacks from outside intruders and must also be cautious about data loss caused by disgruntled employees.
BTech Cyber Security is a four-year program that opens doors to various challenging job roles as Network and Cybersecurity professionals.
The course curriculum focuses on understanding computer networks, cryptography, and ethical hacking, along with practical training.
In this article, we will learn about the purpose of studying BTech in Cyber Security.
This course covers various topics such as:
- Information and Network Security
- Symmetric Encryption
- Advanced Encryption Standard
- Block & Stream Ciphers
- Asymmetric Encryption
- Message Authentication
- Digital Signature
- User Authentication
- Web Security
- Wireless Network Security
- Electronic Mail Security
- Network End Point Security
- IP Security
- Cloud Security
- IOT Security
B.TECH Cyber Security Engineering
Information and Network Security:
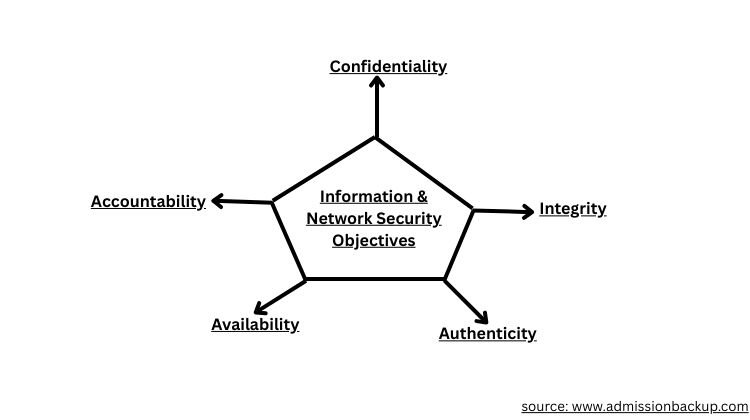
OSI Security Architecture deals with the challenges of Network and Information Security.
As defined by the International Telecommunication Union (ITU-T), the OSI Security Architecture serves the following objectives:
- Data confidentiality and privacy
- Data and system integrity
- Availability or ease of data access
- Data authenticity
- Accountability
Cyber Security Engineers are responsible for the security needs of an organization.
They choose essential IT services to protect the organization from security attacks and design policies for security mechanisms.
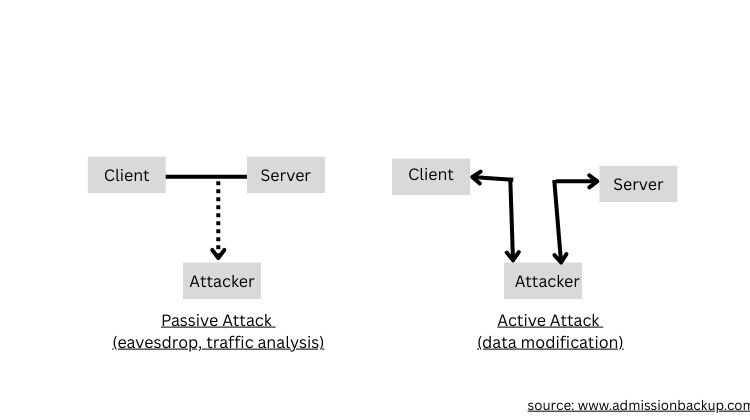
Security attacks are of two types: passive and active attacks.
Passive attacks include eavesdropping or monitoring to obtain information.
Active attacks include modification of messages or data and disruption of services.
Security services include authenticity and confidentiality of data, which can be achieved through various security mechanisms.
Security mechanisms include various methods such as cryptography, password-based login, two-factor authentication, and digital signatures.
Cryptography is the branch of mathematics that deals with the encryption and decryption of data.
Cryptography is of three types:
- Keyless
- Single-key
- Double-key
Keyless algorithms convert data into hash codes.
Example: ABCDEF can be encrypted as 123456.
Single-key algorithms take the data and encrypt it with a public key.
Example: A password-protected bank statement PDF file that opens with a combination of PAN card number and date of birth.
Two-key algorithms involve encrypting the data with a public key made available to all users and a private key specific to a particular entity.
Network security deals with securing computer networks using firewalls.
Computer networks include wireless (802.11) and wired LAN (802.3).
Access points (APs) that provide Wi-Fi access must be password-protected using firewalls.
Firewalls also block most network ports and allow communication mostly through secure ports such as Port 443 for web servers and Port 25 for mail servers.
Port 443 allows encrypted transmission of data packets through Secure Hypertext Transfer Protocol (HTTPS).
Symmetric Encryption:
The process of converting plaintext to ciphertext is called encryption, and restoring the original message from ciphertext is called decryption.
Ciphertext is the encoded message of the original text.
The technique used to decode the ciphertext is called cryptanalysis.
Cybersecurity engineers design cryptographic systems.
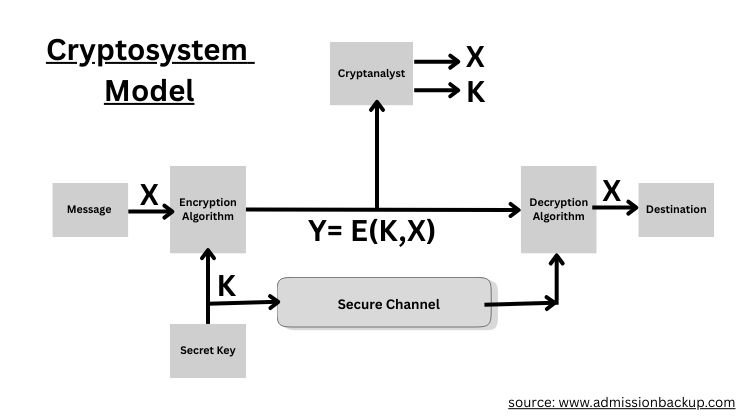
Symmetric encryption is referred to as static or single-key encryption techniques.
The input is the original message, the encryption algorithm is the process of transforming it into ciphertext, and the secret key is an input to the encryption algorithm.
Example of cryptography: Caesar Cipher
It is the earliest known technique, which replaces each letter of the alphabet with a letter standing three places further.
ABCDEF can be written as DEFGHI.
Here, the encryption algorithm is C = (p + 3) mod 26, the decryption algorithm is p = (C − 3) mod 26, and the secret key is 3.
Cryptanalysis attacks rely on the nature of the algorithm and the general characteristics of the original message.
Advanced Encryption Standard:
Advanced Encryption Standard (AES) encodes the data into N rounds based on the key length & four stages.
The number of rounds depends on key length, such as 10 rounds for a 16-byte key, 12 rounds for a 24-byte key, and 14 rounds for a 32-byte key.
The four distinct stages for encoding include substitution of data, shift rows, mix columns & add round key.
AES first converts data into a matrix with n rows and m columns to perform various encoding rounds.
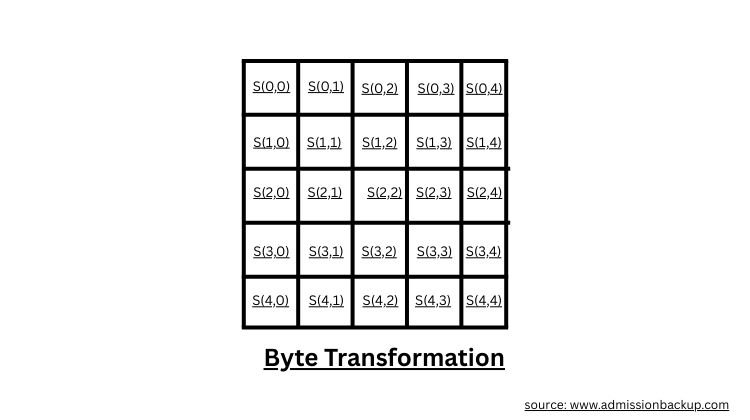
The data is first converted into bits (binary format) to perform these operations.
Each round includes 4 distinct stages of encoding.
The add round key stage holds the information for encryption and decryption, whereas the other 3 stages together provide confusion, diffusion, and nonlinearity.
Each stage is easily reversible (substitution, shift rows & mix columns), & the inverse of the add round key stage is achieved through logic gates using the XOR boolean function.
The stages are defined as Advanced Encryption Standard (AES) transformation functions.
Block & Stream Ciphers:
Block Cipher was developed as a standard for encrypting data stored in sector-based devices such as a hard disk to provide threat protection.
It works on the principle of the Advanced Encryption Algorithm (AES).
Stream ciphers are used for encryption/decryption of data over a communication channel such as file transfer, email, and databases.
They work on the principle of pseudorandom number generation of bits.
Asymmetric Encryption:
Asymmetric Encryption is also known as Public Key Cryptography.
It works on the principle of digital certificates and public & private keys.
Servers, workstations, and software administer certificates, public & private key pairs, including the ability to issue, maintain, and revoke public keys.
Public Key Cryptosystem works on the following algorithm:
- Plain Text: Input to the algorithm.
- Encryption Algorithm: Transformation of plain text.
- Public & Private Key: Public key is used for encryption and the private key for decryption.
- Ciphertext: Encrypted message.
- Decryption Algorithm: Produces plain text.
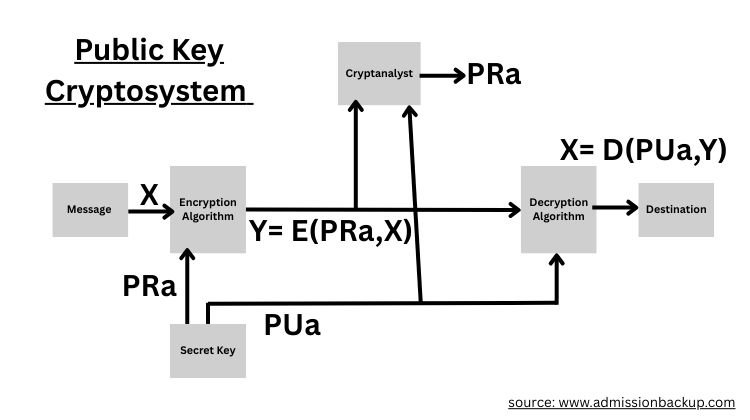
The pair of keys used are: the public key, which is known to all, and the private key, which is kept secret.
The entire encrypted message serves as a digital signature.
The sender encrypts the message with the receiver’s public key, and the receiver decrypts it with its private key.
Message Authentication:
Message Authentication plays a very important role in digital communication.
The transport layer in the OSI Model transmits messages from the sender to the receiver using TCP/IP and UDP protocols.
Checksums are used to verify the authentication of messages.
Cryptographic checksums (or hashes) are unique, fixed-length digital fingerprints generated from cryptographic algorithms known as Secure Hash Algorithms (SHA).
A hash function accepts variable data as input and converts it into a hash value or hash code.
Thus, it becomes computationally infeasible to map data objects using a cryptographic hash function.
Digital Signature:
Digital Signature authenticates two parties who exchange messages over a third party.
It serves the following functions:
- Verify author and data, and time of signature.
- Authenticate contents at the time of signature.
- Must be verifiable by third parties.
The hash value together with the sender’s private key serves as an input to digital signature generation algorithms.
The receiver sends the hash code and the sender’s public key to the digital signature verification algorithm to verify the original message.
User Authentication:
User Authentication plays an important role in organizations for identity management, auditing, and providing access to network resources (file servers, printers, mail servers & internet access).
Using an identity management system, administrators can assign user roles, access permissions, access to workstations, and keep a record of employee information.
Microsoft Windows Server operating systems are widely used in organizations across the globe.

They work on the principle of single sign-on (SSO) & Kerberos.
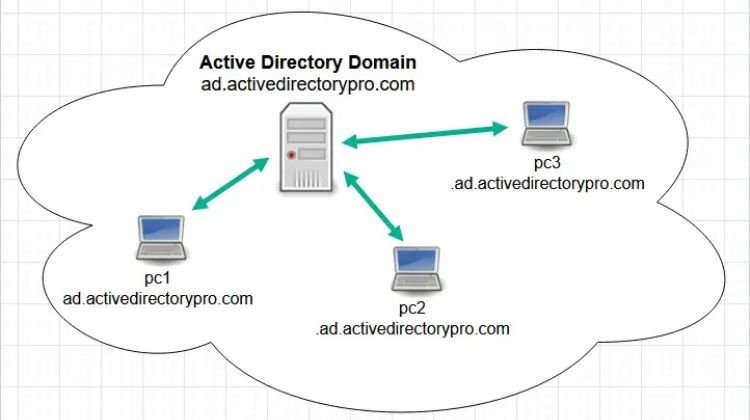
Employees working at different locations can have access to all network resources as their information is stored in Active Directory.
Active Directory is a centralized database of users that provides authentication services to employees in a corporate environment.
All workstations are connected to a centralized server that facilitates user authentication to establish a session and further use network resources in an organization.
Web Security:
Most businesses and government agencies own a website for electronic commerce.
The World Wide Web is fundamentally a client/server application running over the Internet.
Some of the common threats to web security are:
- Modification of user data
- Eavesdropping
- Flooding the server with bogus requests
- Impersonation of a legitimate user
Security can be implemented on the web by using a Secure Socket Layer (SSL) certificate.
An SSL (Secure Sockets Layer) certificate is a digital file installed on a website server that enables encrypted HTTPS communication.
Secure Shell (SSH) is another protocol for secure network communication, used for remote login into servers.
Wireless Network Security:
Wireless networks are more vulnerable to attacks compared to wired networks.
IEEE 802.11 (Wi-Fi) is the standard for wireless connectivity.
Wireless devices such as smartphones, tablets, sensors, and bluetooth devices have limited memory and processing power.
Thus, they are more vulnerable to sophisticated cyberattacks.
Wireless network passwords can easily be cracked by attackers within the Wi-Fi range.
Reducing signal strength to lower limits can prevent attackers from trying to hack the wireless network from outside the building of an organization.
Also, antivirus software and firewalls are commonly used to secure wireless endpoints.
Electronic Mail Security:
Email is a heavily used network-based application.
Some of the most common mail clients used by organizations are Microsoft Outlook and Google Workspace.

A mail server uses various DNS records for sending, receiving, and authenticating email, such as:
- MX (Mail Exchange) records are a type of DNS record that route emails to the correct mail server for a domain.
- Sender Policy Framework (SPF) records are DNS TXT records that list authorized mail servers for a domain, preventing email spoofing and improving deliverability.
- DomainKeys Identified Mail (DKIM) is another DNS TXT record used to authenticate email, ensuring messages are not altered in transmission.
Email spoofing is the most common form of cyber attack.
Verifying the sender domain name can prevent email spoofing.
Network End Point Security:
In an enterprise environment, endpoint devices include servers, workstations, and mobile devices.
Firewalls provide an effective means of protecting endpoint devices from network security threats.
They monitor inbound and outbound traffic and keep a log of internet usage for audit purposes.
A firewall is a physical device inserted between an enterprise network and the internet to establish a security wall.
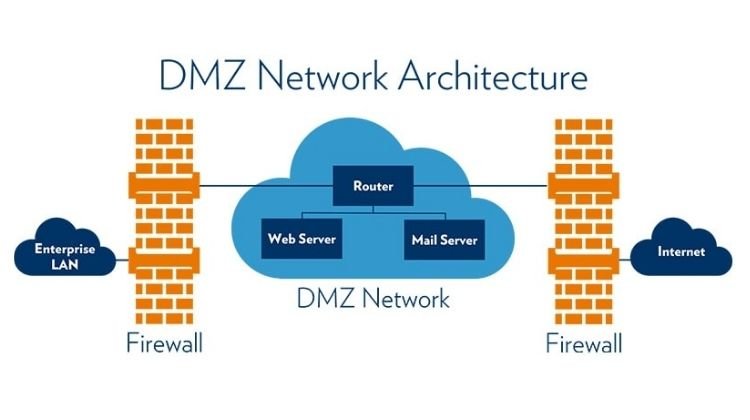
IP Security:
A firewall serves as a platform for implementing a virtual private network (VPN).
VPN uses Internet Protocol Security (IPsec), an open standard used to secure IP communication by authenticating and encrypting data payloads.
It serves as a security mechanism for a wide range of internet applications such as email, client-server application, web access, etc.
IPsec has the capability to secure communication across local area networks (LANs), wide area networks (WANs), and the Internet.
Cloud Security:
Cloud computing is one of the most significant developments in the computing industry.
Cloud provides services under various models such as:
- Software as a Service (SaaS): Plugins and themes to improve website functionality
- Platform as a Service (PaaS): Gmail, Zoom, Google Meet, etc.
- Infrastructure as a Service (IaaS): Virtual machines, AI models, SQL databases, etc.
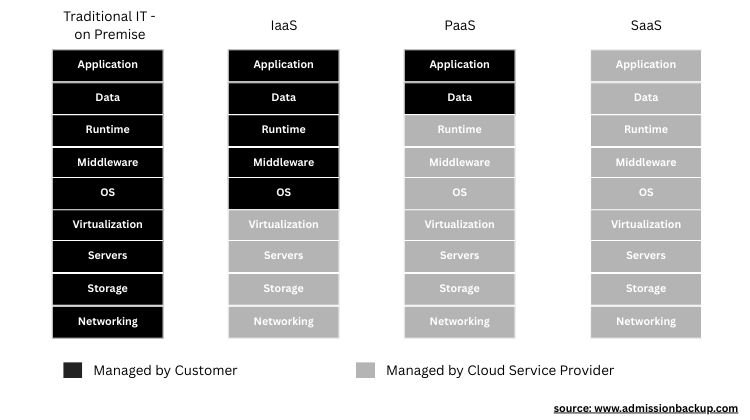
Virtualization plays an important role in cloud computing, as multiple virtual machines can be formed on a single server to host various operating systems such as UNIX or Linux.
As Organizations move their applications and data over trusted cloud service providers (CSPs).
Major cloud service providers hire cybersecurity engineers to provide cloud security.
IoT Security:
The Internet of Things is the latest development in the computing and communication industry.
IoT is an interconnection of smart devices ranging from sensors and cameras used in factories to home appliances such as smartwatches and Amazon Alexa.
IoT components include embedded devices such as microcontrollers, RAM, batteries, transceivers, sensors, and actuators.
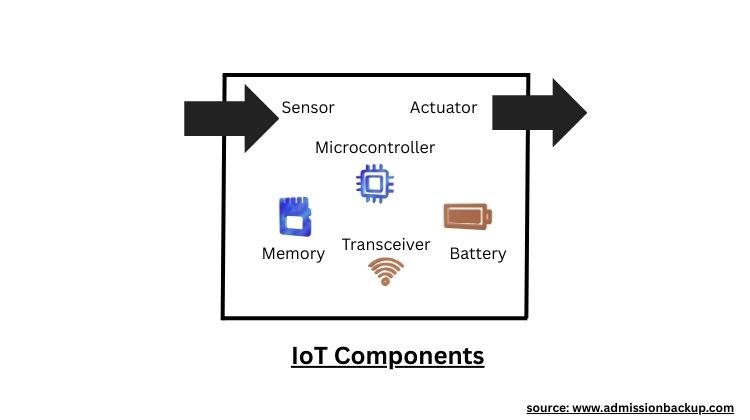
IoT devices have low memory and limited computing capability, as they are smaller in size compared to smartphones, tablets, and workstations.
IoT devices are constrained devices that cannot implement security features such as TLS and IPsec.
Also, software patching is not supported by IoT devices.
Security is a major concern for IoT devices.
MiniSec is an open-source IoT security module.
It is a feature in the TinyOS operating system built for IoT devices.
MiniSec provides data encryption functionality for IoT devices.
B.Tech Cyber Security Admission Process
Students who want to enroll in the 4-year B.Tech Cyber Security program must fulfill the minimum eligibility criteria:
- Must have passed Class 10th and 12th through regular mode.
- Must have studied Science, Mathematics, and the English language in Class 12th.
- Must have appeared in any competitive entrance examination.
Top engineering colleges in Bangalore for B.Tech Cyber Security Engineering:
- BMS College of Engineering
- Ramaiah Institute of Technology
- Dayananda Sagar College of Engineering
- Bangalore Institute of Technology
- Jain University
- Christ University
- Presidency University
- Reva University
- Alliance University
- Dayananda Sagar University
Job Opportunities for Cyber Security Engineers
There are ample job opportunities available after pursuing this course, such as system administrator, cloud engineer, network administrator, and desktop support engineer.
Some of the best organizations hiring cybersecurity engineers include:
- Microsoft
- Amazon
- Broadcom
- Fortinet
- Akamai
- NTT Data
- Cisco
- IBM
- Palo Alto Networks
Average salary package for freshers as cybersecurity engineers varies from 3 lakh to 5 lakh INR CTC per annum.
Medium salary range for engineers with 3 to 5 years of experience varies from 6 lakh to 9 lakh INR CTC.
Highest salary package for cybersecurity engineers ranges between 12 lakh and 20 lakh INR CTC.
Conclusion:
Cryptosystems are built to encrypt the message sent & received between multiple parties.
They provide protection from eavesdropping & brute-force attacks.
Cryptography protocols used in digital communication include Transport Security Layer (HTTPS), Secure Shell (SSH), etc.
They encrypt data using algorithms or programs stored in system memory, using secret keys, hash codes, public & private keys, and digital signatures.
There are millions of viruses, Trojan horses, malicious websites, and hackers present across the world wide web.
B.Tech in Cybersecurity Engineering deals with the study of data protection, securing endpoints, encrypted networks, and user authentication.
For career consultation, please contact our helpline at +91 8546881677.